Updated on: 03/05/2024
Cyberattacks are growing exponentially, and it is estimated that ransomware on a global scale could reach damage costs up to $20 billion. It is therefore important to monitor pages for potential intrusions including malware and malicious link injections on your websites.
The malicious URL automation provides one-click access to page scanning and it can be applied on a single URL or an entire website. This can help to strengthen the cybersecurity of your business and it can also be ideal for sales prospecting. For example, marketing agencies can use this automation to run checks on potential prospects and provide a value-added icebreaker when issues are found.
The Malicious URL checker can be used both on an entire website check or as part of an existing workflow. You can run the automation on-demand or on a schedule.
In this short tutorial, we will cover how to check a list of URLs for potential malware using the following options:
– Using Hexomatic’s ready-made workflow template
– Creating a workflow from scratch
1. How to check pages at scale for malware using Hexomatic’s ready-made workflow
It’s super easy to check malware at scale with this workflow template as it has all the automations incorporated into the workflow.
Simply go to the Workflow Templates section and choose the relevant template to start. You can also click on this link to go to the template page: Check a list of URLs for known malware and malicious URLs
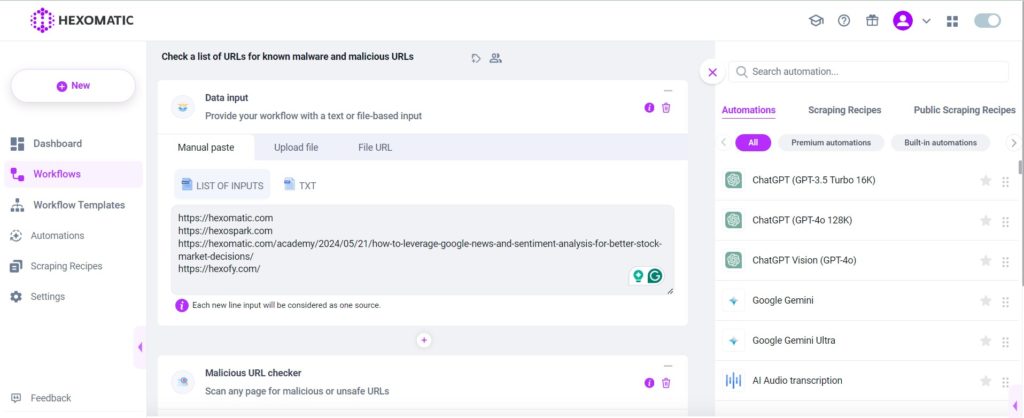
Copy and paste the URLs into the relevant field or upload a CSV file with the URLs.
Run the workflow and get the results in minutes!
2. How to create a workflow from scratch to check pages at scale for malware
Besides using the ready-made workflow to check pages for malware, you can create a workflow from scratch and add the necessary automations manually.
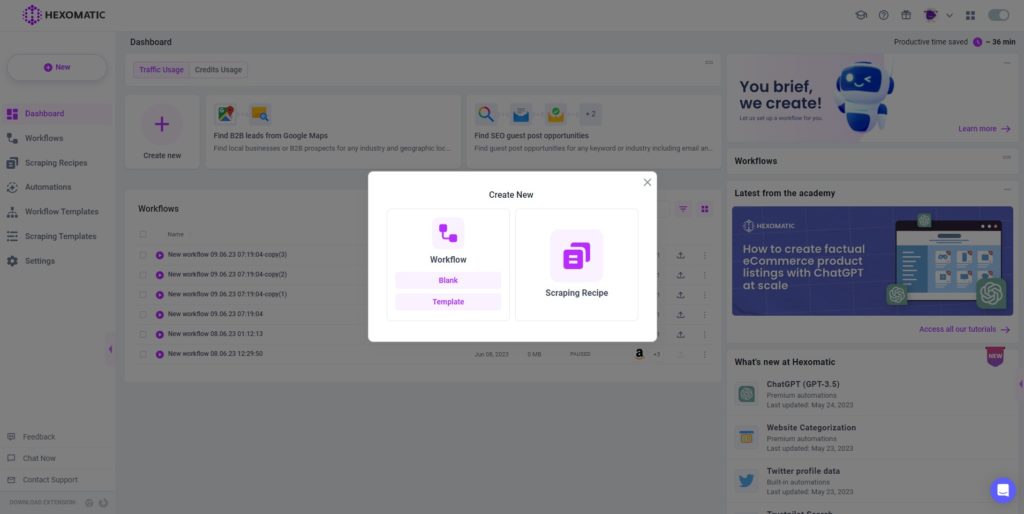
Step 1: Create a new workflow
From your dashboard, create a new workflow by choosing the “blank” option. Then, select Data automation as a starting point.
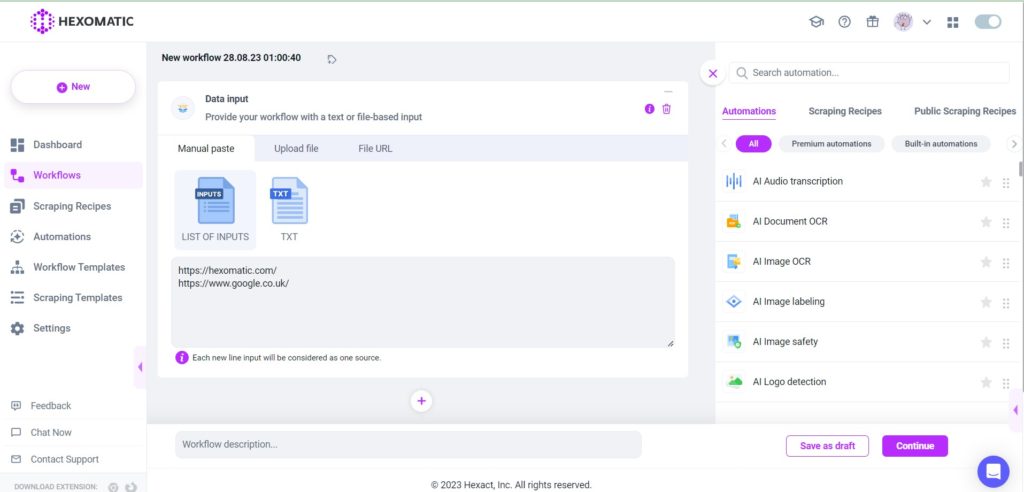
Step 2: Provide a list of URLs
There are two ways you can proceed. You can upload a CSV file containing a list of URLs or you can choose the manual paste option selecting the format as a list of inputs. Then, enter each URL as a new line.
Step 3: Add the Malicious URL checker automation
From the list of automations, select Malicious URL checker and select the data input as a source of the automation. Then click Continue.
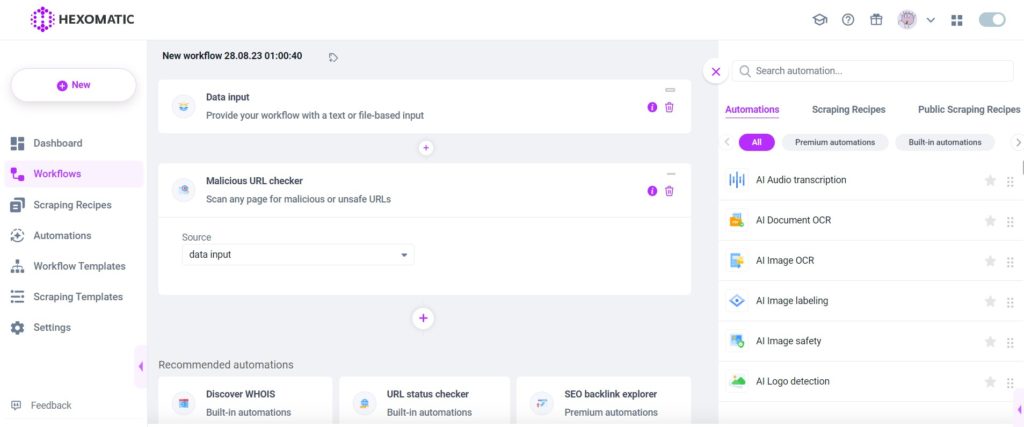
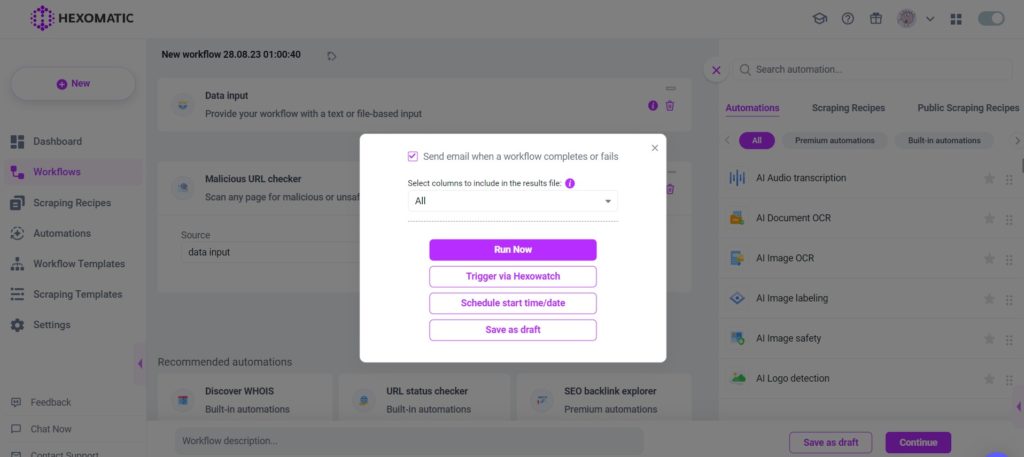
Step 4: Run or schedule your workflow
Next, you can run the workflow or run it on a schedule.
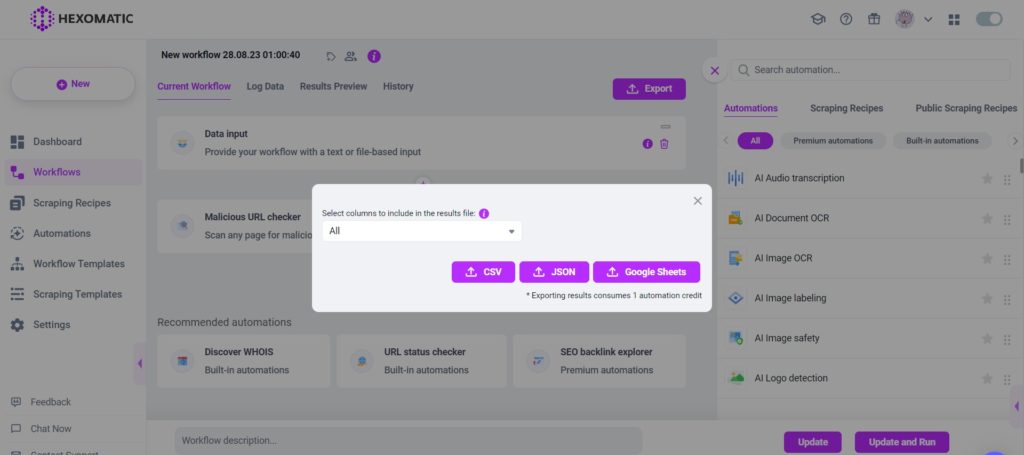
Once your workflow has finished running, you can then review your data in the Results Preview and export it in CSV or Google Sheets.
Main use cases for malicious URL checker
| User Group | Reason for Use | Benefits |
|---|---|---|
| Business Owners and IT Managers | To strengthen cybersecurity by monitoring for malware and malicious links. | Prevents cyberattacks, protects sensitive data, and maintains website integrity. |
| Marketing Agencies | To check potential clients’ websites for cybersecurity issues as a value-added service. | Enhances service offerings, builds trust with prospects, and provides a strong icebreaker. |
| Sales Teams | To use security checks as an icebreaker in sales pitches. | Demonstrates value to prospects, differentiates from competitors, and initiates conversations. |
| Web Developers | To ensure the websites they develop are free from malware and malicious links. | Ensures the delivery of secure websites, protects reputation, and provides added value to clients. |
| Cybersecurity Firms | To provide ongoing monitoring and security audits for clients. | Delivers comprehensive security solutions, builds long-term client relationships, and enhances service portfolio. |
| E-commerce Websites | To safeguard customer data and maintain trust by regularly scanning for threats. | Protects customer data, prevents financial losses, and maintains brand reputation. |
| Educational Institutions | To secure their online platforms and resources from potential cyber threats. | Protects student and staff data, ensures continuity of online learning, and maintains institutional reputation. |
| Government Agencies | To safeguard public websites and portals from cyber threats. | Protects sensitive public data, ensures the reliability of online services, and maintains public trust. |
Automate & scale time-consuming tasks like never before
Marketing Specialist | Content Writer
Experienced in SaaS content writing, helps customers to automate time-consuming tasks and solve complex scraping cases with step-by-step tutorials and in depth-articles.
Follow me on Linkedin for more SaaS content
